A couple months ago I received an email from Namecheap, the registrar used for my ethans.link domain. The email read (some parts omitted):
Hello Ethan,
We are contacting you from the Namecheap Legal and Abuse Team […]
It has come to our attention that phishing content is displayed on your website at the link:
[link in question]
redirects to
[phishing site]
The email goes on to include Namecheap’s abuse terms and requests a prompt correction and response within 48 hours, otherwise the domain would be suspended.
After the initial fright of getting a rather serious looking email had passed, my reaction was to of course check for the existence of the link in question. Unsurprisingly, I was able to confirm that it had indeed been created, along with a handful of other links redirecting to similar sites that had not yet been reported. I quickly destroyed the links and wrote back stating that I had taken care of the issue. Namecheap responded the next day confirming they had reviewed the case, confirmed the removal of the malicious content, and that the issue report was now resolved.
At the time I didn’t think much else of this other than the fact that it was somewhat surprising someone had actually found my link shortening service and was using it maliciously. Though in hindsight it’s honestly not that surprising that the first person to actually use my personalized link shortening service other than myself would be someone with indecent intents.
A month or so passes and I try to use one of the shortened links I had created a while ago, except when I click on the link, my anti-virus pops up saying the link has been blocked for being malware. Once again I was startled at first and had to confirm that my website hadn’t been compromised somehow, but after checking the server and logs, the only thing I found was that more phishing links had been created.
At this point I realized some of the inevitabilities that creating a link redirecting service would bring, and it occurred to me that simply destroying the links on a regular basis would not be a sufficient means of preventing abuse.
After once again solving the problem by removing the new set of malicious links, I took to the internet to see what I could learn about link redirecting/shortening services (perhaps the research I should have done before even starting the project?). My searching quickly led me to a fantastic blog post (which also happens to be the inspiration for this write-up) by the creator of y.gy titled: How I Accidentally made my Link Shortener into a Malware Honeypot. Sound familiar?
Maya, the author of the article, came to the conclusion that the only real way to prevent abuse, was to paywall the service. Now I’m not entirely sure I agree that’s the only way to solve the issue (after all bit.ly and many other link shortening sites with free services exist), but the overall point still stuck. There’s a lot of complexity to preventing abuse with a link redirector. For someone like me who never had any intent to monetize my site, or even any intent for it to be used by others, this approach didn’t make much sense. After all, the only reason I created ethans.link was because I thought it’d be cool to have a personalized link shortener. In my infinite wisdom, I never even conceived that people other than me would use it, and certainly not for malicious reasons. Making the portal to ethans.link public was mostly so I could show off my pet project to others, and because it takes less work than the alternative.
So with this newly minted knowledge of reality in mind, I came to the conclusion that I would have to take down my site. Except that’s a pretty lame conclusion to come to, and I still wanted to be able to use the personalized links I had created for myself. So, instead it was time to lock down access to the site. I had already been using Authelia to control access to some other projects, so I simply added a rule to ethans.link to add it to the protected sites, which is why if you try to visit the portal now, you’ll be asked to sign in. Anyone can still access the links I create, for example ethans.link/mywebsite will take you to my website, but only I am able to create links now.

But what about the problem of my anti-virus now blocking my site? I could just add an exception and be done with it, but then if I ever send one of my personalized links to someone else, would they have the same issue? Even just as a point of pride, did I really want the site that I own and host to be classified as malware? Not really. I decided to put ethans.link into virustotal.com to see what was going on.
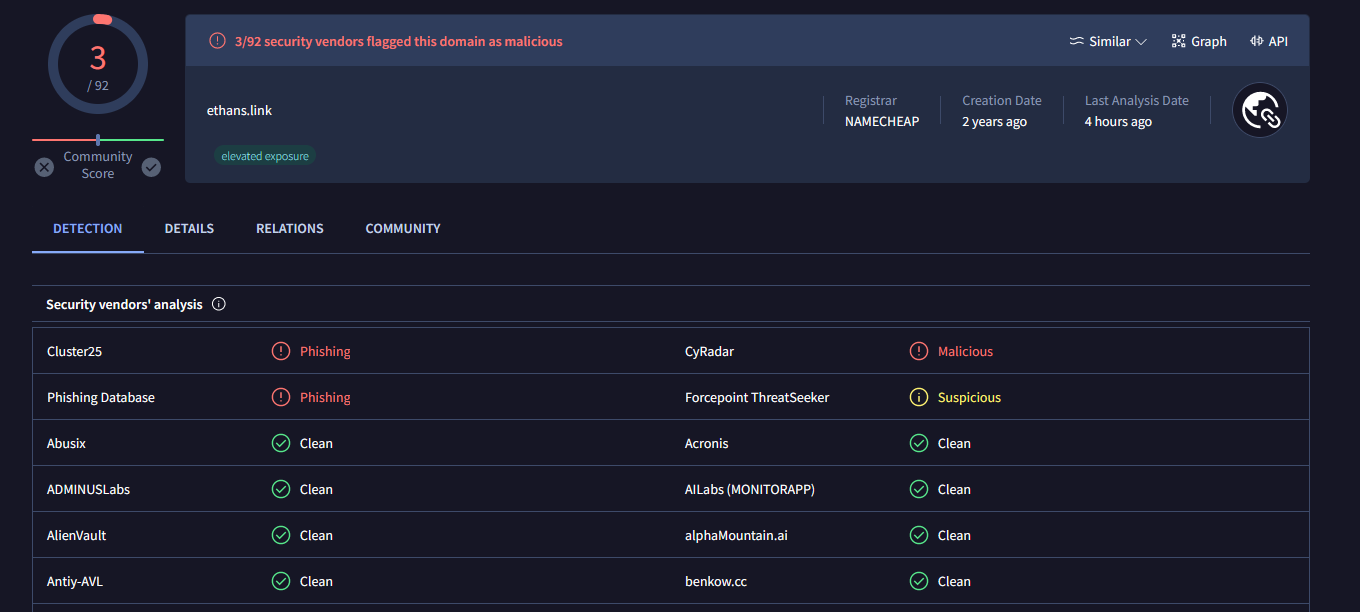
Virus Total aggregates data from numerous security vendors to assess risk of files and websites alike. Querying for my site, I found that 15 different security vendors had classified my site as one of malware, phishing, malicious, or suspicious. Once again the reality of what I’d created set in, and I was admittedly ashamed for not having the foresight to see this coming when I made the project two years ago. Honestly the only surprising fact of this outcome is that it took so long.
Fortunately, Virus Total maintains a list of contacts for all the security vendors, and it was mostly just a matter of going through the various emails and forms to submit requests for reassessment and correction to my website’s classification. At the time of writing, I am down to only three vendors outright classifying the site as dangerous, and one as suspicious. Hopefully this number will eventually make its way back to zero once they’ve all had time to re-review.
So obviously some things were learned from this whole experience. Similar to Maya, I had been naive about the service I was making and how it could be used. If nothing else, I hope to be a little more considerate about what I am creating and putting out into the world. And despite me writing this mostly because I thought it would be fun to share my experience with some family and friends, if anyone else does read this, I hope that it is because unlike me, you are researching your product before creating it, and not finding this post after you’ve already discovered the same issue.